Sectrio released the findings of its 5th OT and IoT Cybersecurity Threat Landscape Assessment and Analysis report today. The comprehensive report covers details such as threat actors, malware, breach tactics, at-risk sectors, quantum and quality of cyberattacks, and specific threats to OT and IoT deployments and critical infrastructure around the world.
The section on North America offers some insightful data points on the OT and IoT threat landscape in the region:
- Ransom cost per GB of data held by hackers is now $39000
- Energy, Healthcare, manufacturing, utilities, maritime, and defense are among the most targeted sectors
- Overworked SOC teams and lack of visibility into some of the infrastructure played some businesses right into the hands of hackers
- Mining sector could be targeted in 2022 as there is rising hacker interest in this sector
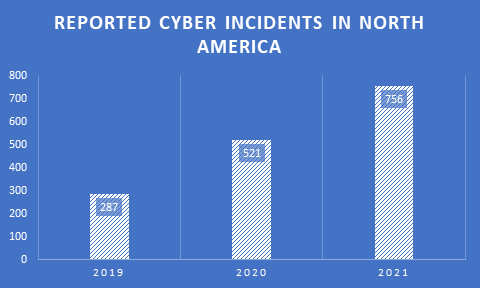
- 756 major cyber incidents reported in the region in 2021
- Highest remote ransom demand $50/70 Mn (Various sources)
- Ransom recovered: $6 Mn (Forbes, Nov 2021)
- The rise in average ransom demand: 71 percent (Sectrio)
- Hack campaign cycles intercepted: 71 (Sectrio)
Hackers are now targeting widespread disruption and huge ransoms through targeted cyberattacks. While the geopolitical motivation in many of these attacks remains at a very high level, the expansion of botnets in Mexico poses a new security risk to businesses in the region. Manufacturing facilities in Mexico are also being subject to high levels of reconnaissance probes by hackers.
Some actors are carrying out localized attacks from within the region using sophisticated phishing kits developed in parts of Eastern Europe and the Middle East. We came across many such kits that were modified to some extent to target businesses in US and Mexico. These kits are now freely available on the web but sophisticated APT groups such as Lazarus and Fancy Bear could be embedding them with trojans to control the networks and data in businesses targeted by these local hackers.
This is a new tactic that APT groups are using to widen their net. By offering free phishing kits, they are allowing other groups to conduct the initial hacking work while they lurk in the background waiting to jump networks or digital assets to reach a target asset which could be a critical infrastructure facility or a defense installation.
In all, the malware load in the traffic analyzed by our team has grown significantly in the last 6 months of 2021. This over-the-board increase will definitely put an additional strain on the already overworked SOC teams managing the security needs of businesses in sectors such as manufacturing, utilities, and others. Hackers are specifically targeting control systems and connected IoT devices. The former to cause disruption and the latter to target third-party infrastructure such as websites, critical servers, and even mobile phones.
Supply chains, the new target
Supply chains are presenting hackers with a moving and lucrative target. In addition to large-scale disruption, such attacks also offer more return on investment. In addition, other factors make supply chains a favorite for hackers:
- The opportunity to strike businesses from multiple entry points
- Once infected, malware can move across the connected infrastructure crossing not just organizational but even political boundaries
- The entry of start-ups with high valuation and risk appetite but with low appetite or patience rather bring systems online in a foolproof way after a cyber incident. This means that these companies may be more susceptible to paying a ransom to get things back on track faster
- Workflows, responsibilities, and systems are not aligned towards cybersecurity imperatives today
- Hackers may also be aware of zero-day vulnerabilities across vendors that are yet to be discovered
Specific challenges with OT in North America
While investments in IT security have grown, OT cybersecurity investments and attention are still lagging. Businesses that are hosting complex hybrid environments or are connected to IT, OT, and the Internet of Things are now gradually understanding the importance of ramping up their cybersecurity measures to align them with the complexity involved in securing such environments. However, the hackers are miles ahead of them as they are well aware of these cybersecurity gaps than the cybersecurity teams protecting them.
Businesses hosting complex environments without adequate security cover are closer to a massive cyber disruption than they can imagine.
- Some businesses have upgraded their OT environments by adding new devices. Such devices are however invisible to standard off-the-shelf vulnerability scanners.
- OT vulnerability scans are not done frequently and many businesses fail to fall back on a more disciplined approach that requires regular scans and remediation
- The ever-evolving OT and IoT threat landscape throws up new threats including malware that evade detection
- Visibility into threat surfaces is not adequate. Some of the solutions used by businesses are prone to misconfiguration and new vulnerabilities.
- OT security teams in many instances are less empowered than their IT counterparts and if the same security team is handling both IT and OT cybersecurity, OT doesn’t get as much attention as it should
Such critical gaps in addressing OT cybersecurity across the infrastructure leave the room wide open for hackers or other adversarial entities to exploit.
You can read more about such threats in the 2022 Threat Landscape Assessment and Analysis Report prepared by Sectrio’s research team.
What is the 2022 IoT and OT Threat Landscape Assessment and Analysis Report all about?
The 2022 Threat Landscape Assessment Report prepared by Sectrio’s Threat Research team tracks and documents the evolution of IoT, OT, and IT cyber threats and their implications for businesses across the globe. It answers many questions that are puzzling cybersecurity decision-makers and other stakeholders alike. Where are the threats coming from? Why are certain sectors getting attacked more often? Which groups and countries are behind these attacks and more importantly what tactics are they using and what impact could such attacks have on businesses in 2022?
It is a must-read for everyone who wishes to understand how the cyber OT and IoT threat landscape changes around the world can impact them and their business. You can download the report here.
Try our rich OT and IoT-focused cyber threat intelligence feeds for free, here: IoT and OT Focused Cyber Threat Intelligence
Planning to upgrade your cybersecurity measures? Talk to our IoT and OT security experts here: Reach out to sectrio.
Visit our compliance center to advance your compliance measures to NIST and IEC standards: Compliance Center


Get access to enriched IoT-focused cyber threat intelligence for free for 15 days