Highest amount of Cyberattacks recorded in India
While yesterday was a big day for cricket fans in the Indian sub-continent. Cricket teams from India and Pakistan clashed in a T-20 encounter as part of the ICC Men’s T20 World Cup in Dubai. While the match was being held, we were able to record some interesting developments in cyberspace.
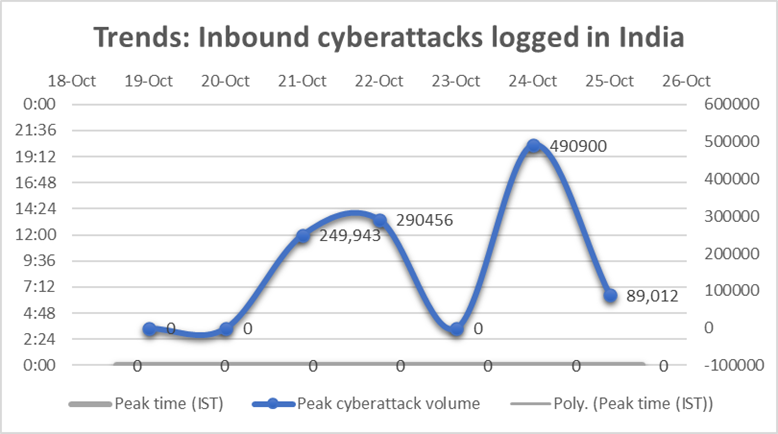
For the last 6 days, the number of inbound cyberattacks logged by our physical and virtual honeypots in India held steady in the region of about 3,00,000 attacks a day. On October 24th, however, the number of attacks rose substantially to hit the 490000 mark briefly before dipping significantly towards midnight Indian Standard Time. The cricket match was over by then. We are only considering the sophisticated attacks here (this does not include reconnaissance or low-grade probing).
Most of the cyberattacks were coming directly from IP addresses belonging to a certain country to the West of India (no prizes for guessing). There were also a few IP addresses from South East Asia and Eastern Europe that were participating in these attacks. These IP addresses belonged to known botnets which meant that they were being leveraged for coordinated event-based cyberattacks on the country.
While the spike in cyberattacks connected to a geopolitical event is now commonplace, it is the first time that such cyberattacks have been linked to a sporting event involving teams from the sub-continent.
Geopolitical developments and cyberattacks
Sectrio has in the past shown the links between geopolitical developments and cyberattacks in the Middle East, North America, and Southeast Asia. The mode of operation is more or less the same in all the cases which are that every spike in the volume of cyberattacks logged by our honeypot networks is linked to a geopolitical development in the region.
State-sponsored actors or nation-state groups are often behind such attacks. Third-party actors affiliated with state-backed actors are also activated by nation-state groups (or specifically their controllers) to increase the impact of such attacks. Even states that are not recognized by the United Nations have their own hacker groups that participate in such attacks. These groups earn foreign exchange or specifically hard currency for the treasuries of the states involved.
The cyber armory deployed by such groups has diversified in recent years with the induction of stealthy ransomware and advanced military-grade malware developed and sold by agencies backed by the cyber intelligence wings of nation-states. Malware dumps in the Dark Web and malware procured from groups that steal them from academic institutions and private labs and sell them through forums are also used in such attacks after modifying them enough to evade detection and to hide their origin.
Every possible outcome including disruption, espionage, and theft of critical and confidential information, deployment of trojans for long-term spying, and infrastructure monitoring are pursued by such groups. The targets include critical infrastructures such as water treatment plants, power grids, oil and gas infrastructure, key manufacturing facilities, stock exchanges, and defense installations.
To deter such cyberattacks, critical infrastructure needs to be secured on priority. OT elements, IoT devices and networks, and IT-based systems need to be diagnosed for vulnerabilities and cyber risks using sophisticated cybersecurity tools like micro segmentation, Vulnerability management, and contextual threat intelligence. Till such a time that cybersecurity receives more attention and action, such attacks will continue to grow in scale and impact.





