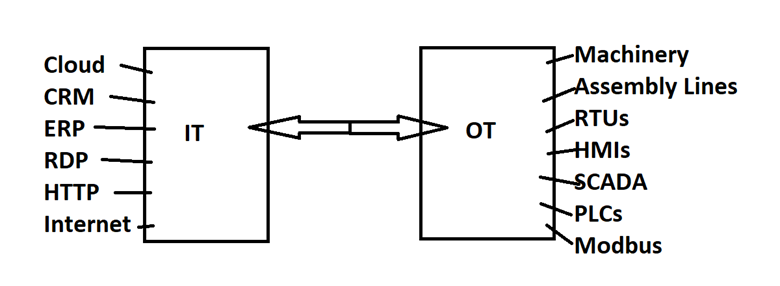
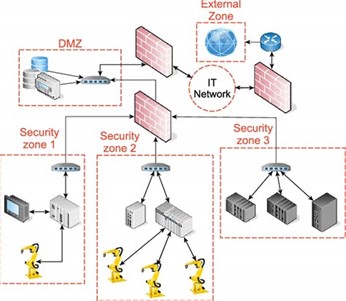
As industrial businesses connect their OT and IT networks, network segmentation is becoming an increasingly important approach. Using this method, it is feasible to successfully secure industrial assets while maintaining their important characteristics.
Data reigns supremacy in the era of the Industrial 4.0 Revolution. In some of our most important industries, it catalyzes IT/OT convergence. IP subnet-based VLANs and utility infrastructure are being combined in smart cities like Dallas to detect water use and leaks, enabling intelligent water saving.
The industrial and manufacturing sectors are also implementing IoT solutions to gather crucial data from machinery and production lines. Companies are cutting project schedules, limiting unplanned downtime, lowering operational costs, and witnessing growth never seen before. Security considerations must, however, moderate the desire for efficiency and profitability since the security of an entire organization’s vital infrastructure is on the line.
In an OT environment, traditional IT segmentation is inadequate. We have depended on strong perimeter security for many years to monitor communications related to north-south traffic at the network level. However, the construction of traditional IT segmentation including intricate VLAN and firewall setups takes time. Additionally, OT settings have a low tolerance for extended downtimes, particularly when it comes to pipelines, power plants, or ports of call.
Additionally, IT firewalls can’t completely reveal which set of packet exchanges are permitted in an OT context.
Micro segmentation is becoming more and more of a realistic option for lowering OT attack surfaces as a result of the sophistication of cyberattack methods. Current statistics show that “connectivity to external systems continues to be the predominant root cause of…incidents, a sign that enterprises still fail to adopt network segmentation best practices.”
Micro-segmentation allows for fine-grained workload visibility. It offers improved breach containment for OT settings, zero trust security, SDN-based control, granular control of systems that must adhere to regulatory standards, and SDN-based control.
What is OT Network Segmentation?
OT networks from IT networks, guest networks from corporate networks, and essential industrial networks are all separated from one another via network segmentation, a physical security measure.
Within essential infrastructures including oil and gas, electricity, utilities, aircraft, transportation, manufacturing, and other important verticals recognized by the US government, segmentation is frequently used. Why? Because ICS devices and the computers used to monitor and control them require increased attention due to the increasing attack rates and degrees of competence needed to access them.
Why are OT network segmentation and segregation essential?
The significance of segregation has been underlined frequently over the past few years, particularly in light of the recent spate of significant data breaches, including those at Marriott, Equifax, WannaCry, and many more. Network isolation can prevent malware, but how? Segregation enables you to separate the infection and stop it before it gets to the network’s core if your first virus or ransomware defenses are breached. By doing so, you and the IT staff at your company will be able to limit the breach to a single host before you need to take manual action.
Using advanced methods, an attacker may attempt to connect straight from a compromised host to a more susceptible host. The Australian Cyber Security Centre reports that once a workstation has been compromised, the hacker frequently attempts to establish a remote connection to a server, map a network resource, or use authorized network administration tools to access sensitive data or run malicious code on that server.
Therefore, the key to assisting you in preventing such assaults is a well-planned and implemented network segregation and segmentation. Some preventative measures include setting servers to restrict file sharing, forbid remote desktop connections, and limit the server’s capacity to interact with distant connections.
The risk of Unsegmented OT-IT Networks
Flat Network – All of the equipment in the facility is interconnected and forms a flat network. There is no compartmentalization, segmentation, distinction, or prioritizing since any device can “speak” to any other device, from the telephones at the help desk to the webcams at the point of sale to the desktops in accounting. No incline, so flat. Although flat networks are quite popular, there are several significant concerns that you should be aware of.
Shopify Inc., a multinational Canadian e-commerce business, published a security incident alert on its website on September 22, 2020. Two workers were discovered to have illegally accessed documents about some of the company’s merchants. According to estimates, the issue exposed customer information from 200 vendors, including names, email addresses, addresses, and order details.
Shopify released the following statement in response to the incident: “We promptly revoked these people’s access to our networks and reported the situation to police enforcement. In the investigation into these criminal activities, we are presently collaborating with the FBI and other foreign organizations. Although there is currently no proof that the private data was utilized, the company has informed the impacted merchants of the occurrence.
One of the largest security issues that businesses are currently experiencing is insider threats. User behavior analytics (UBA) is used by ManageEngine ADAudit Plus to assist IT, and security teams, in identifying insider threat signs such as numerous unsuccessful login attempts, unusual user behavior such as a spike in file accesses, or privilege escalations. ADAudit Plus uses machine learning to establish a baseline of typical user behavior and only alerts security staff when this baseline is violated.
Implementing OT Network Segmentation: 5 Best Practices
Threat actors now view OT factories as simple, low-effort ventures with a good probability of significant payouts during the past 10 years. Factory owners put a lot on the line when there are lockouts, and they frequently dive deep into their coffers to pay ransoms rather than accept the chance of losing days of availability. The foundation of current OT security trends is the illusion of protection that perimeter firewalls and air gaps provide. They are unable to stop hackers with the dexterity to travel laterally who are ready to observe and wait for months to finally get access to the relevant security credentials. They are also helpless against risks brought inside by negligent or malevolent insiders.
Regardless of the technology used, there are five best practices to follow to perform network segmentation and segregation effectively:
1. Network Layers
Applying technology to more than simply the network layer is strongly advised. It is necessary to separate and segment each host and network. As long as it is practically possible, even the smallest host and network should be divided into the smallest possible segments. This kind of strategy mostly applies to the data connection layer and includes (but is not limited to) the application layer. There are, nevertheless, circumstances in which private information necessitates physical seclusion. It should be highlighted that continual central monitoring of these kinds of defensive network measures is necessary.
2. Principle of Least Privilege
A network or service shouldn’t be permitted to interact with another host or network if it isn’t necessary. Therefore, if a certain host or network only needs to “speak” to another service or network using a particular protocol, it should stick to that. By putting these guidelines into practice, you will strengthen your organization’s overall security posture and complement the reduction of user rights.
3. Hosts and Network Separation
It’s also a good idea to separate networks and hosts based on how crucial your company’s commercial activities are. This contains multiple platforms, based on distinct security domains and classifications for certain networks or hosts. For sensitive situations, take into account physically isolating “out of band” management networks as well as segregating management networks.
4. Increasing the Authorization Process’s Focus
Access to all other users, hosts, and services should be available to each one. Additionally, access should only be granted to those who need it to carry out their allocated activities and obligations. Everyone who violates the requirements for authorization and authentication should be closely watched and, if necessary, deactivated.
5. Whitelisting of Network Traffic
Instead of restricting access to unwanted traffic or blocking a particular service, only valid network traffic that has been verified and approved should be permitted. This method will produce a useful security policy tool for blacklisting and improve your organization’s ability to prevent and identify possible network intrusions.
Flexible deployment options and support for different technologies are available for internal segmentation. Cost and how much change is required for implementation are the two main factors to consider while picking solutions. For instance, a Software Defined Network (SDN) can segment a business network, but it requires a substantial investment and the installation of a whole new network topology. The deployment of solutions that integrate fast, transparently, and can adapt to the factory’s possible mixed architecture of new, legacy, and unpatched assets is necessary to maintain optimal utilization and availability around-the-clock.
5 OT Network segmentation advantages
- Enhanced Security — It is possible to separate network traffic and block connectivity between network segments.
- Access Control Improvements — Permit users to access just the particular network resources that are necessary.
- Better Monitoring – You can now identify questionable activities and take steps to lessen them.
- Better Performance – Local traffic is reduced because there are fewer hosts per subnet. Broadcast traffic can be separated using a local subnet.
- Better Containment: If there is a network breach, the damage is contained to the local subnet.
OT security network segmentation best practices
While dividing networks into IT and OT segments is a nice place to start, it is insufficient. Within the OT/ICS network, new sub-perimeters, zones, and conduits must be defined to implement more preventative or investigative controls, have greater contextual visibility, and be protected from any compromises.
The Purdue Enterprise Reference Architecture Model
ISA’s Purdue Reference Model (PRM), a system of classifying technologies based on their criticality to cyber-physical processes, should be used to analyze the environment and its traffic flow.
Also learn: Threat modeling using the perdue model
To segment the OT/ICS network, it is common to manage the network architecture using enterprise reference models such as:
- Purdue Enterprise Reference Architecture (PERA)
- IEC 62443, a 3-tier IIoT consortium
- European Union Agency for Cybersecurity also known as ENISA
- National Institute of Standards and Technology (NIST): NIST CSF self assessment
- The OT security guide
- The SANS ICS 410
and/or a combination of these models.
PERA is a reference architecture that can represent the enterprise at different architectural lifecycle stages and in different layers:
- Level 0: Physical process, field devices, and equipment control (defines real physical processes) (e.g., valves, pumps, motors, etc.).
- Level 1: Local control (controllers for local cells, lines, and processes, distributed control system (DCS) controllers, programmable logic controllers (PLCs), remote terminal units (RTUs), etc.) and intelligent devices (sensing and controlling physical processes, such as process sensors, actuators, analyzers, and related instrumentation) for cell, line, and process, etc.
- Level 2: Control systems, real-time controls and software, DCS, human-machine interface (HMI), supervisory and data acquisition (SCADA) software, local alarm servers, process analytic systems, and other comparable systems to level 3, but not merely plant-wide.
- Level 3: Laboratory, maintenance, and plant performance management systems; Managing the production process to create the required goods; Batch management; Manufacturing execution/operations management systems (MES/MOMS); middleware and data historians linked to; shifts, hours, minutes, and seconds
- Level 4: Business logistics systems; directing the manufacturing operation’s business operations; The main system is enterprise resource planning (ERP); which identifies the fundamental production schedule, material usage, transportation, and inventory levels for the plant; Months, weeks, days, and shifts are the time frames.
- Level 5: Enterprise/IT Networks; Cloud; Financial; ERP-type Systems/Applications; Internet Demilitarized Zone (DMZ); Server Management (email, web, proxy, etc.).
- IIoT: Interacts and crosses layers 1–5.
- Safety systems: Isolating safety systems as much as feasible inside their segments with significant regulatory boundaries in place is a best practice that is advised.
KEY TAKEAWAYS
The key insight is that the more segmented the network is:
- the harder it can be for a hacker to breach your systems;
- the additional time it takes to design/manage the internal network;
- the harder it takes for users to access all the information in the network
In summary, thorough network segmentation is crucial for enterprises, especially when it comes to preventing possible threats. You may divide your network into different zones with the aid of a solid segmented network architecture, and then strictly manage and enforce the rules governing what is permitted to flow from zone to zone. It is advised that you create distinct network segments for your various needs and limit interconnectivity to what you really must have access to. It will be challenging to control a data extraction scenario if, for instance, servers in your company that are used for financial reporting are accessible from the main office network or the guest Wi-Fi at the reception. As a result, the effects of this might be disastrous for the company.