While the colonial pipeline cyberattack has brought in a renewed interest in critical infrastructure cybersecurity, it is important to note that from the year 2015, there have been cyberattacks of low magnitude recorded globally. These include reconnaissance attacks as well as disruptive attacks. Such cyberattacks have gradually expanded in scale and intensity in recent times. In the pandemic era, hackers have shown a new level of zeal in attacking critical infrastructure deployments globally.
Why are the hackers turning so confident and how can their disruptive tactics be challenged and thwarted? Let us examine some ways.
Background
On Friday (May 7th), The Colonial Pipeline that carries 2.5 million barrels a day which accounts for 45% of the US East Coast’s supply of diesel, petrol, and jet fuel was taken offline by its operator after a ransomware attack. The FBI has officially confirmed that it is investigating the incident along with the operator and various government agencies are chipping in to help.
Attacks on critical infrastructure have risen significantly in the last two years. The increase in the number of Advanced Persistent Threat groups, threat actors with access to sophisticated tools and tactics, and the emergence of independent actors have all contributed to this trend. Here are a few more reasons for the rising attacks on critical infrastructure:
- APT actors started monetizing cyberattacks in 2020. This could be because some of the state-backed hackers found their funding reduced in the pandemic era.
- Extensive reconnaissance activity in 2018.,2019 and 2020 enabled hackers to get plenty of network and privilege information that is now being used by hackers to exploit networks and assets.
- Evolution of complex and hard-to-detect ransomware. Malware developers are now merging the capabilities of various malware to evolve hybrid variants that are hard to detect and contain.
- Employees working remotely using access facilitated by unmonitored networks.
- The year 2020 also saw the weaponization of the greatest number of vulnerabilities.
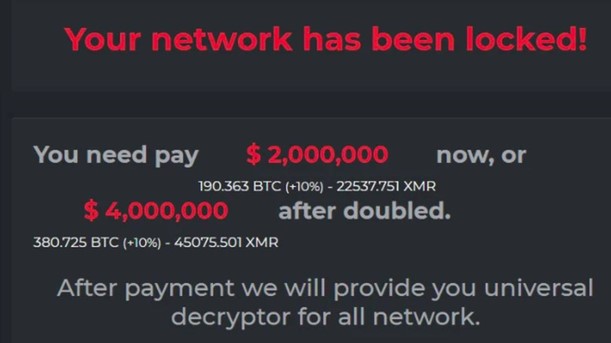
Addressing the critical infrastructure cybersecurity challenge
Among the many measures that can be deployed to prevent such large-scale breaches and disruption, one approach stands out. Defense-in-depth, which involves building multiple layers of opportunities to detect attacks early and prevent them can help critical infrastructure operators expand the gap between critical assets and hackers.
In addition, to countermeasures, defense in depth also covers the adoption of a rigorous compliance mandate that includes reliability regulations at various levels, preparation efforts, and enhancement of employee skills to strengthen the mechanism to prepare for, respond to and recover from any incident with minimal or no disruption.
Without such holistic measures, the fight against cybercriminals and state-backed threat actors will always yield partial results and lead to the emergence of more emboldened hackers in the future.
The clock is ticking.
The Further you delay, the greater the threat becomes. Subex Secure can help detect threats in real time and mitigate them immediately.





