End-to-End OT and IoT Security Solutions Provider
Sectrio offers the most comprehensive and holistic cybersecurity solutions, consulting, and risk assessment approach to secure your entire OT/ICS and IoT footprint

Path to NIS 2 Compliance
Sectrio can help you comply with NIS2 well before the deadline. Lets work together to secure your OT/ICS and IoT Infrastructure.

















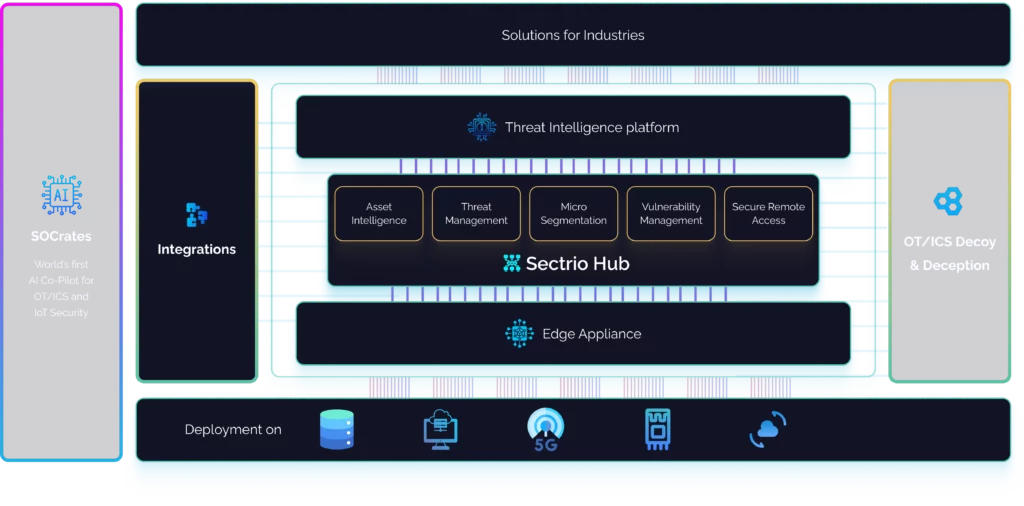
Solve Your Biggest OT/ICS and IoT Security Challenges with Sectrio
Cybersecurity Solutions Engineered to Deliver Optimized OT/ICS Protection

SOCrates
World’s first AI Co-Pilot for OT/ICS and IoT Security
Consulting & Managed Services

Compliance Services
Why Sectrio?

One Stop Solution for OT/ICS and IoT Security
A curated portfolio to secure your entire OT-IT and IoT connected ecosystem
Designed to operate seamlessly across systems and networks
Build ground up by Sectrio unlike other fragmented solutions

Largest IoT and OT Honeypot Coverage
We capture and analyze over 22,000,000 attacks in a day
Curated threat intelligence feeds to keep you ahead of adversaries
Actionable and contextual threat intelligence feeds that can be ingested easily

OT/ICS and IoT Industry Expertise
Qualified team of OT and IoT security experts to guide you every step of the way
Vast domain expertise and certfied professionals to catapult your threat hunting initiatives
Operate smartly and swiftly to defend against sophisticated cyberattacks



One Stop Solution for OT/ICS and IoT Security
Accurate threat detection, prevention, and remediation on one platform
Harden systems for the highest levels of protection
Manage security posture with granular attention
Largest IoT and OT Honeypot Coverage
Over 22,000,000 attacks analyzed each day
Gain a deeper view into the tactics, techniques and procedures used by threat actors
Widest coverage of cyber threat sinks and malware origin sites
OT/ICS and IoT Industry Expertise
Batches of qualified OT and IoT security experts with trench experience
Proven expertise in designing and executing governance and compliance strategies
Primed to enhance value, lower risk exposure, and improve security outcomes
How Sectrio Can Help You?
Optimized Protection Across Industries

Manufacturing
Protect your ICS, IIoT, and OT environments with high levels of visibility and granular control
Know More

Manufacturing
Protect your ICS, IIoT, and OT environments with high levels of visibility and granular control.
Know More

Oil and Gas
Prevent emerging and known threats from disrupting operations, breaching systems and exfiltrating data.
Know More

Oil and Gas
Prevent emerging and known threats from disrupting operations, breaching systems and exfiltrating data.
Know More

Airports
Aviation asset security, data integrity, vulnerability management and protection against malicious interference in operations
Know More

Airports
Aviation asset security, data integrity, vulnerability management and protection against malicious interference in operations
Know More

Smart Cities
Fortify your smart city: Secure the entire digital landscape, safeguard systems and data at scale.
Know More

Smart Cities
Fortify your smart city: Secure the entire digital landscape, safeguard systems and data at scale.
Know More

Manufacturing
The manufacturing sector has a mix of legacy systems that are converging with IT networks creating cybersecurity weak points.

Oil and Gas
Consequences of cyberattacks include infrastructure damage, prolonged supply disruptions, and safety challenges.

Smart Cities
Rising cyberattacks on smart cities are mainly attributed to hackers seeking ransom by encrypting citizen data

Utilities
OT systems could potentially be hijacked to shut down generation, cause surges or damage to substations and other infrastructure.
Solutions Designed For You

Knowledge Transfer
Facilitate sessions to help IT understand OT/ICS intricacies.
Joint Incident Response Teams
Establish joint IT-OT incident response teams.

Unified Security Policies
Develop unified security policies aligned with IT and OT requirements.

Collaborative Vendor Assessments
Assess vendor cybersecurity collaboratively.

Process Familiarization Sessions
Familiarize IT with industrial processes.
Collaborative Strategies
Develop joint segmentation strategies for IT and OT systems.

Collaborative Risk Assessments
Conduct joint risk assessments considering IT and OT perspectives.

Unified Solutions
Implement unified monitoring and anomaly detection mechanisms.
Don’t Just Take Our Word For It



Awards and Recognition
Sectrio is proud to be recognized as a leading OT and IoT security solutions vendor by some of the most influential voices from across the globe.
Latest Blogs
Complete Guide to ISA/IEC 62443-3-2: Risk
ISA/IEC 62443-3-2 is a globally recognized standard designed specifically to address the unique cybersecurity challenges...
Read MoreCyber-Physical Systems Security Analysis Challenges and
Securing our data’s authenticity has become quite the challenge in today’s era of smart living....
Read MoreComplete Guide to OT/ICS Security in
Electricity, a resource often taken for granted, is the lifeblood of our modern world, powering...
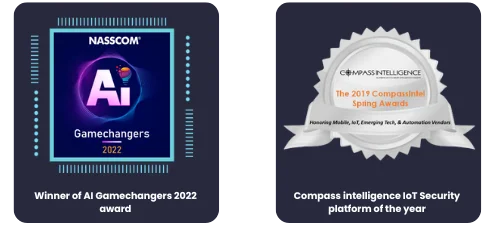
Read MoreCoverage
Norway
Sweden
New Zealand
Sydney
Indonesia
Singapore
Malyasia
Japan
Hong Kong
Myanmar
New Delhi
Bangalore
Mumbai
Saudi
Dubai
Kuwait
Qatar
Botswana
Ghana
Ivory Coast
Turkey
Italy
Ukraine
Portugal
Spain
Poland
France
UK
Finland
Lithuania
Toronto
Houston
Denver
Seattle
San Francisco
New York
Mexico
Bogota
Brasilla
Buenos Aires
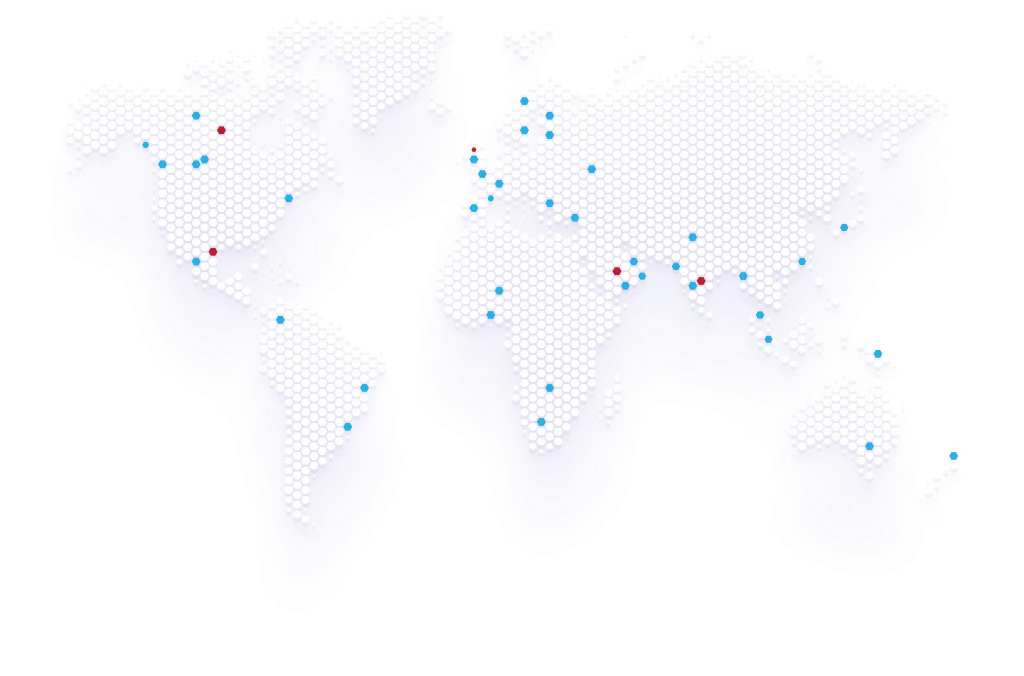
Dubai
Mumbai
Banglore
Singapore
London
Sydney
Hongkong
Myanmar
NSHM Knowledge Campus
Qatar
Kuwait
Saudi Arabia
Sweden
Malta
Spain
Portugal
Ivory Coast
Ghana
Ghana
Johannesburg
Botwaswana
Brasilia
Buenos Aires
Santiago
Bogota
Toronto
Seattle
Westminster
- Security Operations Center
- Honeypot Locations