Hackers have decided to latch on to the excitement generated by the ongoing T-20 World Cup in Australia. Over the last two weeks, Sectrio’s threat research team intercepted/came across 20 emails that were targeted at senior executives from the government, manufacturing, oil and gas, healthcare, and utility sectors. From the data available, we can infer that most emails and WhatsApp messages were targeted against businesses or government entities based in India while Australia, Singapore, and South Africa were ranked 2nd, 3rd, and 4th respectively in terms of the volume of communication reported by recipients.
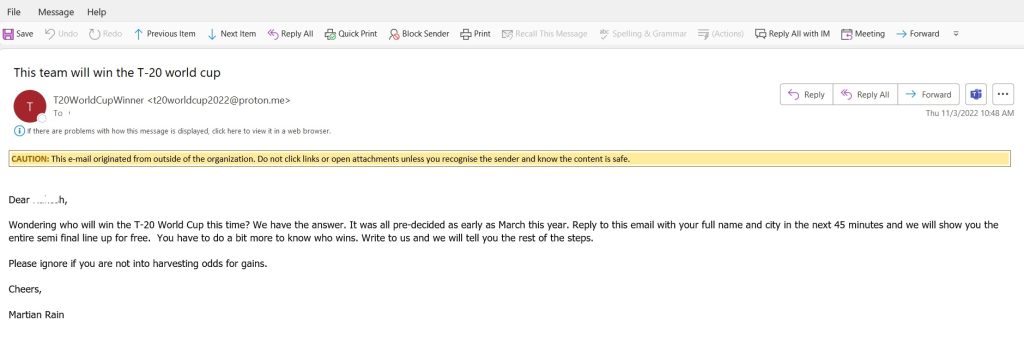
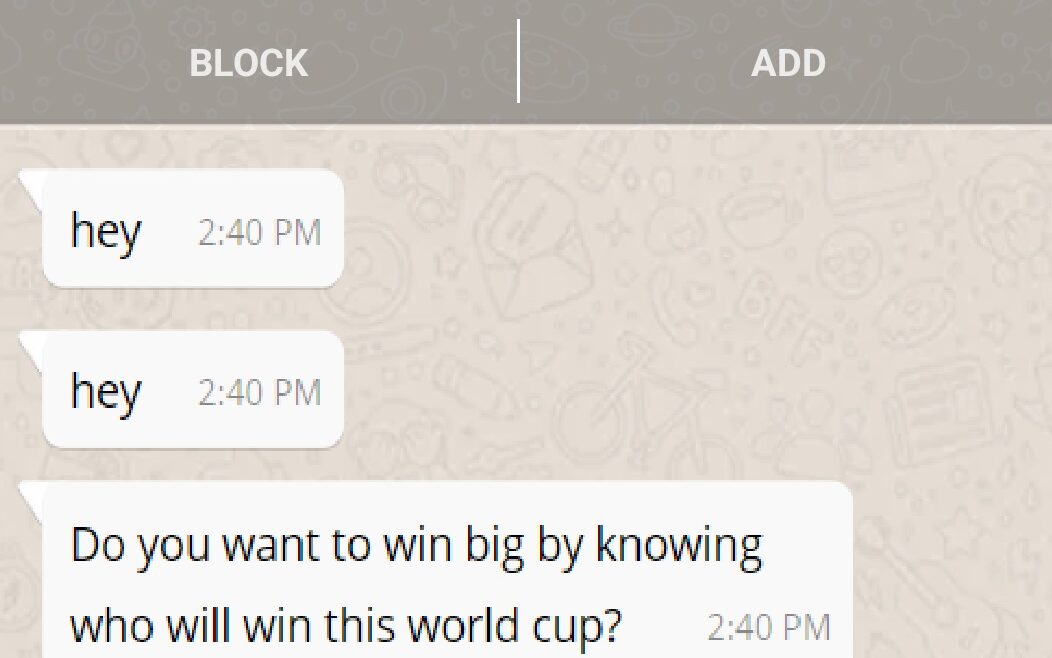
Most emails claimed to know which team would eventually lift the trophy this month and encouraged recipients to use that knowledge to place bets with a leading sports betting agency in England. Once a recipient replies to an email, they are further asked to share personal information (which could be used to hack their online accounts or validate information already harvested from other sources) on the pretext of giving more information.
Some of the recipients also received a link that takes them to a website infected with crypto-mining malware.
How are the hackers ramping up their targeted phishing campaigns?
While topical attacks based on trending sports and geo-political events are not new, this campaign run by hackers adds a new dimension to the problem of protecting businesses against involuntary insider activity that might lead to a compromise of data or credentials. Hackers are clearly ramping up their game in terms of identifying specific trends to use as well as specific targets within organizations to reach out to.
While latching on to topics that are more likely to elicit a response, the scammers behind this campaign are also planning to harvest data for long-term targeting. In terms of targeting machines, the malware used was a new version of well-known crypto-mining malware called Nitrokod which has been around for a while now. First detected in 2019, this malware lured victims to download desktop versions of popular mobile apps. Once downloaded, the malware stays latent for a period of almost 45 days keeping a low signature by running multiple processes in the backend to hide its footprint. The actual infection is triggered much later.
After a communication line is established with the hacker by the malware, information on the infected machine is passed on. By delaying the infection process, the malware avoids detection in sandbox environments.
Sectrio’s threat research team is still evaluating the malware and we will be able to share more information on the new variant soon.
We are giving away threat intelligence for free for the next 2 weeks. Find out how you can sign up and try out our threat intelligence feeds

Find out what is lurking in your network. Go for a comprehensive 3-layer threat assessment now






