When the year began, few businesses and cybersecurity vendors had imagined the extent to which the cybercrime landscape globally would deteriorate. Subex’s threat research team had started seeing a clear increase in targeted cyberattacks. We, therefore, decide to call out this trend and in early March, we came out with our first advisory.
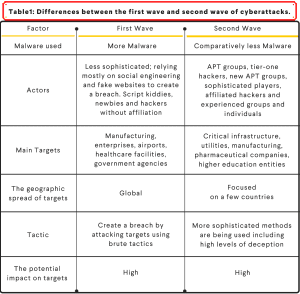
The cyberattacks that saw a spike in the last 180 days emerged in two distinct waves. The first wave included more actors, malware, variants of malware, and geographies and was designed to exploit the confusion created by the Covid-19 pandemic. The second wave had lesser moving parts, was more organized, and in many ways built upon the success of the first wave.
From our analysis, the second wave of attacks is still gathering momentum and will continue for at least another 65 days. We expect the attacks to slow and move into reconnaissance mode after that.
Key trends
- Cyberattacks on Chinese interests globally and in China rise 230 percent
- The majority of the attacks on China are emerging from just 4 countries
- Attacks on datacenters and utility firms increase the most
- Phishing attacks continue to rise
- Most attacked regions – NA, South-East Asia and the Middle East
- Attack on pharmaceutical manufacturing companies; increasing rogue activity detected; targets include attempted batch and recipe changes as also operational disruptions to reduce the production capacity
- Variants of NotPetya are being discovered across manufacturing firms
- Coronavirus-themed attacks evolve
The second wave of the Coronavirus-themed attacks grew more specific and potent towards mid-May. Chatter on the Dark Web and closed-door forums picked up indicate that there were many successful breaches in the last 90 days with many firms giving in to the demands of the hackers by meeting the ransom demand placed by hackers. Regional, businesses in Europe handed over the maximum amount in ransom to hackers followed by South East Asia and the Middle-East. - In terms of frequency, at least one ransom was paid every 43.2 hours by some company somewhere. In some instances, APT groups in Pakistan, Russia, Iran and some other countries were also involved in multi-stage ransomware attacks. So why have APT groups resorted to monetizing their cyberattacks? One probable reason could be because in the aftermath of Covid-19, many governments have shrunk their black ops/cyber offense budgets and this must have hit the APT groups in countries that were already under sanctions, starved of funds for their cybercrime operations. It seems that some of these countries have authorized monetization of cyberattacks to keep the operations sustainable and to prevent erosion of cyber strike and malware development capabilities.
- A threat actor based in Somalia/East Africa launched as many as 700,000 attacks in a just under four days and walked away with a huge bounty in ransom. This group seems to have used stolen credentials available on the web along with compromised apps inadvertently installed by victims. This group targeted oil and gas companies in the Middle East.
- While deflective attacks on critical infrastructure came down this quarter, the attacks on this segment kept on rising. While the initial half of the second wave of attacks on critical infrastructure used Covid-19 themes to a large extend, the latter half of attacks used more targeted messaging and tactics.
IoT and OT cybersecurity solutions and strategies are definitely the need of the hour.
Read more about these threats and security challenges in the latest edition of our Threat Landscape Report for Q2, 2020





