When LockBit 3.0 was launched in June, the group touted it as the most powerful encryptor ever built. The launch also led to a 17 percent rise in cyber incidents directly linked to the encryptor. The new variant brought in new features such as more payment options across cryptocurrencies, new monetization options, and more means to recover or destroy data as per the outcome of negotiations with the victim. The files were not just encrypted but exfiltrated as well to put additional pressure on the victim.
A typical attack begins with the victim’s device being infected and the files being encrypted with a jumbled extension. The process of data encryption is done at a rapid speed with multiple tasks being done in parallel. The infection becomes apparent with the wallpaper of the victim’s machine being changed to a ransom note. In case the ransom is not paid on time, the victim’s data is then put up for sale on the Dark Web and other forums.
Sample of LockBit 3.0 Ransome Note
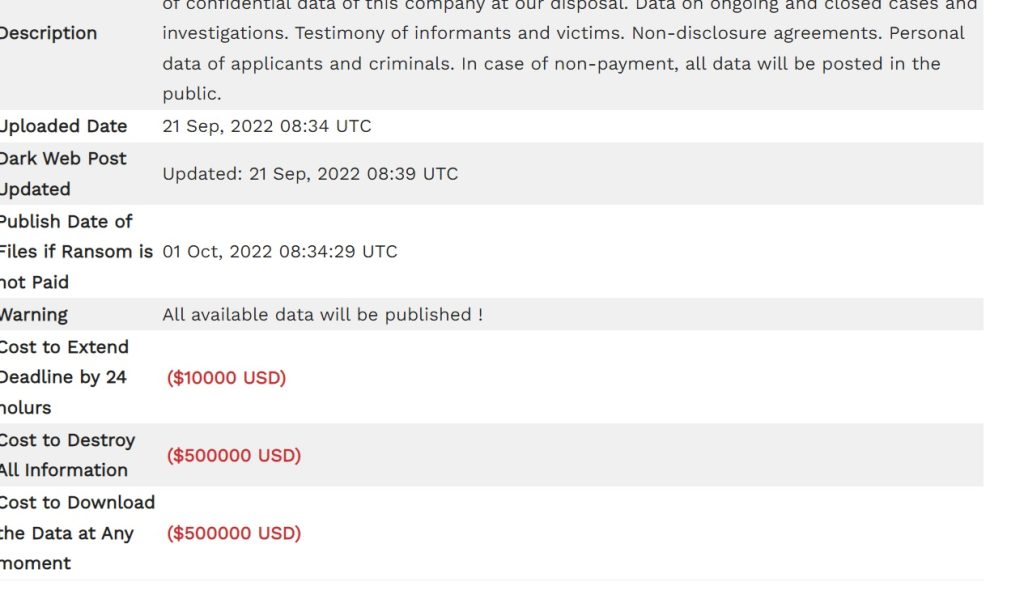
At the time of writing this blog post, we did come across an APAC enterprise that was successfully targeted by the LockBit 3.0 group. The ransom note asked the victim to pay $10000 to extend the deadline by 24 hours, $500000 to destroy all information, and a similar amount to download the data at any time.

LockBit 3.0 was much in demand in Ransomware as a Service market. Which explains the sudden and steep rise in LockBit 3.0-linked attacks.
The group even ran a bounty program to incentivize the detection of bugs in its code. LockBit operators were keen on preventing non-group members from obtaining the decryption tool. Since it was first detected in the wild in mid-June, LockBit 3.0 has been reported consistently from over 33 honeypot locations of Sectrio indicating its prevalence and global presence. It even outcompeted rivals such Hiveleaks and Blackbasta in infecting maximum victims since launch as documented by Sectrio’s threat researchers.
For a while, everything seemed to be going the way of LockBit 3.0 developers until an alleged disgruntled developer threw a spanner in the works by releasing the code of the encryptor which subsequently made its appearance on Twitter at least a couple of times. This will enable other ransomware groups to build on the encryptor (or modify it) and launch new and more stealthy variants.
What’s next for LockBit 3.0 and other ransomware groups?
New ransomware groups could theoretically launch their operations with these modified variants. Such variants could also be re-engineered in academic or research labs and in case these variants are accidentally or deliberately released into the web in the future, then the chain of attacks linked to LockBit 3.0 will continue to worry cyber defenders for months or even years.





